#How secure is your data with data recovery services
Explore tagged Tumblr posts
Text
How secure is your data with data recovery services?
Data recovery services prioritize data security by using encrypted connections and secure storage. They have confidentiality agreements to protect your privacy. https://www.datarecoveryinmalaysia.com/ Choose a reliable service with a good track record and consider backing up your data regularly and using strong passwords for added protection.
data recovery Malaysia
1 note
·
View note
Text
Preventative IT Maintenance: Keeping Your Business Running Smoothly

With technology moving forward so fast, your business can’t operate without it. Computers, servers, cloud systems and software platforms have to be running smoothly to keep your team productive, defend confidential information and make sure customers receive a good experience.
Unfortunately, IT systems don’t manage themselves without attention.
This is why we need preventative IT maintenance. Regular car servicing makes sure your car avoids breakdowns and preventative IT support does the same for your systems. Here at Image IT, we know that companies who focus on IT before issues arise benefit a lot. We’ll now look at what preventative maintenance means and understand why it helps your business run smoothly.
What Does Preventative IT Maintenance Mean?
Taking care of your IT infrastructure ahead of time is called preventative maintenance. With preventative maintenance, you take action to make sure your systems are in good shape all the time, so you don’t have to rush to solve emergencies.
Such tasks refer to:
Tracking how the system is running
Putting security patches and new versions of the software into use
Regularly using antivirus and malware software
Testing the use of backup options
Updating both your device’s drivers and firmware
Checking the configurations for firewalls and networks
Exchanging ageing equipment to prevent any breakdowns
At Image IT, we set up specialized maintenance services that guarantee your technology remains in top condition and reduces the chance of risks and downtime.
Why Taking Care of Problems in Advance Is Crucial for Companies in Ireland
1. Minimize any time when your business is not working effectively.
Problems with your IT systems such as servers failing, networks breaking or bugs in software, may bring your work to a halt and cost you in both time and money. Doing preventative maintenance lets you catch and manage issues early and this means your business avoids the stress of dealing with major problems.
If a server begins to overheat, it’s possible to handle the issue before it crashes, so you won’t have to deal with expensive downtime and loss of data.
2. Prevent or Stop Cyber Attacks
More and more, businesses in Ireland are facing cyberattacks, most often small and medium-sized companies. Many attackers use old software, unpatched versions and networks that have not been properly set up.
Ongoing upkeep of security tools such as firewalls, antivirus software and system updates, makes it much less likely for your system to become a victim of ransomware, phishing or a data breach.
3. Increase the Lifespan of IT Assets
Just as changing the oil in your car lengthens its engine’s lifespan, looking after your IT equipment in the same way will help it work longer. Regularly taking care of computers stops them from wearing out and prevents too many replacements.
4. Raise the effectiveness of your staff.
This kind of slow work is frustrating and influences how your team feels about their work. If technology runs smoothly, your team won’t have to worry about systems or spend time finding IT solutions.
5. With time, the cost of IT will decrease.
Though it might feel like a pricey addition, upfront maintenance helps save money and prevents serious IT problems. One data breach, meeting replacement or lasting period of downtime can often be more expensive than all your ISP’s services put together.
Important Parts of a Well-Made IT Maintenance Plan
We create preventative maintenance strategies for your business that fit its individual requirements at Image IT. The method we use is:
We watch your systems around the clock.
We watch over your systems around the clock, spotting problems early and fixing them so they don’t impact your work.
Timely Updates and Patch Upgrades
We make sure your operating systems, applications and antivirus are always running on the latest versions.
Test the backup and recovery of your data.
We ensure your backups are properly configured and we regularly perform tests to see how fast you can recover data.
You can do a Network Health Check here.
We examine your network for good speed, serious security flaws and technology issues to confirm your system operates safely and properly.
Managing Assets and Deciding on Their Life
We watch over your equipment and make sure you can update your technology before it starts causing issues.
Support from the users and helpdesk
If your team has any IT questions or concerns, our friendly team is there to lend a non-technical helping hand.
Why Is Image IT a Great Solution?
Operating out of North Dublin, Image IT has been supporting company’s in Ireland for about 15 years. Our knowledgable team delivers helpful, consistent and friendly IT assistance to the companies here in New Zealand.
We are dedicated to forming long-term relationships with clients so we can do more than just address issues; we can help avoid them.
You will gain the following benefits when you work with us:
Transparent pricing
A quick response from the team
Customized maintenance services
Expert opinions offered in a personal way
If you have just a few devices or a complex IT structure, our solutions are designed to match your requirements and your budget.
Benefits You Can See in Life: An Example
There were many issues at one of our clients, a small financial services firm in Dublin, involving downtime in the network and software that was past its update. Following their sign up for our preventative maintenance, we set up a monitoring system, cleaned their network and ran scheduled updates.
The result? A 90% drop in IT issues reported by staff, faster systems, and peace of mind for their management team knowing their data and systems were protected.
Your Next Step: Secure Your Business with Preventative IT Support
Don’t wait for a system failure, data breach, or productivity drop to remind you of your IT vulnerabilities. Preventative maintenance is one of the smartest investments you can make in your business.
Let Image IT take the stress out of managing your technology — so you can focus on what you do best.
2 notes
·
View notes
Text

How Server Location Impacts Your Website
Choosing the right web hosting service is critical to the success of any online presence. Among the various factors to consider, server location stands out as a key element. Server Location refers to the geographic location of the data centre where your website’s files and data are stored. While it might seem like a technical detail, its influence on website speed, performance, and user satisfaction cannot be overstated.
Website Speed and Latency
The closer the server is to your website visitors, the lower the latency or delay in data transfer. For instance, if your server is located in Europe but your target audience is in Asia, the physical distance can cause delays in loading time. Faster websites not only create a better user experience but also encourage visitors to stay longer. Research shows that users are more likely to leave a site if it takes more than a few seconds to load, making server proximity critical for reducing bounce rates.
Boosting SEO Performance
Search engine optimization (SEO) plays a vital role in driving organic traffic to your website. Server location directly affects page load speed, which is a crucial ranking factor for search engines like Google. Additionally, if your website is targeting a specific region, having a server in that region can enhance its visibility in local search results. This geotargeting benefit can give your site a competitive edge in regional markets.
Enhancing User Experience
Modern internet users expect instant results when browsing websites. A server closer to your target audience ensures they can quickly access content, stream videos, or complete transactions without delays. A smooth user experience not only improves customer satisfaction but also increases the likelihood of conversions, whether it’s a sale, a subscription, or another desired action.
Meeting Legal and Compliance Requirements
Different regions have distinct laws and regulations regarding data storage and privacy. For example, the General Data Protection Regulation (GDPR) in the European Union mandates strict control over the storage and processing of personal data. Hosting your website on a server in a compliant region helps you meet these legal requirements. This ensures your business avoids fines or legal complications while building trust with your users.
Data Security and Reliability
Server location also influences the security of your website. Data centers in certain regions are better equipped to handle threats, including cyberattacks and natural disasters. Locations with advanced cybersecurity infrastructure and disaster recovery systems provide an added layer of protection, ensuring your website remains operational even in adverse conditions.
Global Reach with Content Delivery Networks (CDNs)
If your website targets a global audience, relying on a single server may not be sufficient. Content Delivery Networks (CDNs) can help bridge the gap by distributing copies of your website across multiple servers worldwide. This ensures faster delivery of content to users regardless of their location. CDNs optimize the user experience and help businesses scale efficiently.
Conclusion
The server location in web hosting is a fundamental factor that impacts the speed, accessibility, and reliability of your website. It influences user experience, search engine rankings, data security, and legal compliance. When choosing a web hosting service, prioritize server locations that align with your target audience and business goals. By making an informed decision, you can ensure a faster, safer, and more successful online presence for your website.
3 notes
·
View notes
Text
Why Working with a Certified Financial Advisor Makes Financial Sense?

*"It's not about timing the market, but time in the market"* - Warren Buffett
In today's complex financial landscape, navigating investment decisions can feel like trying to sail through a storm without a compass. Recent data from the Financial Conduct Authority shows that 27% of UK adults have low financial resilience, highlighting the critical need for professional guidance in financial planning. As we venture into 2025, the value of working with a certified financial advisor has never been more apparent.
1. The Numbers Don't Lie: The Impact of Professional Guidance
The proof is in the pudding, as Brits would say. According to a 2023 Vanguard study, working with a financial advisor can add up to 3% in net returns annually through proper wealth management strategies. This phenomenon, known as "Advisor's Alpha," isn't just about picking investments – it's about comprehensive financial planning that considers your entire financial picture.
Furthermore, research by Russell Investments revealed that 76% of investors working with financial advisors felt more secure about their retirement plans compared to just 43% of those managing investments independently. This peace of mind, particularly during market volatility, is invaluable.
2. Beyond the Basics: What Certified Advisors Actually Do
Let's be crystal clear – a certified financial advisor isn't just someone who helps you pick stocks or mutual funds. They're qualified professionals who must complete rigorous training and maintain ongoing education requirements. In the UK, Chartered Financial Planners must complete over 14 modules of advanced financial planning topics and accumulate at least five years of relevant experience.
Their expertise extends to:
- Tax-efficient investment strategies (saving clients an average of £2,700 annually according to St. James's Place Wealth Management)
- Estate planning and inheritance tax mitigation
- Retirement planning with consideration of the latest pension legislation
- Risk management and portfolio diversification
3. The Long-term Value Proposition
While many hesitate at the thought of advisor fees, consider this: The Money Advice Service reports that 78% of UK adults who worked with financial advisors for over five years said the advice they received was worth more than the fees paid. This long-term perspective is crucial, especially when considering that properly managed portfolios have historically outperformed self-managed ones by an average of 1.5% to 2% annually over the past decade.
At 12% Profit, we've observed that clients working with certified advisors typically achieve more consistent returns and stay invested during market downturns, avoiding the costly mistake of emotional decision-making. Our analysis shows that advised clients were 45% more likely to maintain their investment strategy during the 2020 market volatility, resulting in significantly better recovery outcomes.
Making the Right Choice
*"The best investment you can make is in yourself"* - Peter Lynch
Choosing to work with a certified financial advisor is about more than just investment returns – it's about creating a structured approach to achieving your financial goals. Whether you're planning for retirement, saving for your children's education, or building long-term wealth, professional guidance can make a substantial difference in your financial journey.
Remember, as Warren Buffett wisely noted, *"Price is what you pay, value is what you get."* In the realm of financial advice, this couldn't be more accurate.
---
*Would you like to learn more about how professional financial guidance can help you achieve your financial goals? Visit our website or schedule a complimentary consultation with one of our certified advisors.*
3 notes
·
View notes
Text
BisonSol ($BISON): A Comprehensive Overview for Next-Generation Cryptocurrency Trading
1. Introduction to BisonSol
High-Speed Transactions: Built on Solana, one of the fastest and most scalable blockchain networks, $BISON enables swift transactions with minimal fees.
Cutting-Edge Trading: The platform’s aim is to offer advanced trading capabilities, allowing users to access a wide range of cryptocurrency assets from a single interface.
Community-Centric Approach: BisonSol is designed with its community in mind, ensuring that new features, products, and services align with user feedback and industry best practices.
2. Advantages of Holding $BISON
Reduced Fees: By leveraging Solana’s low transaction costs, holders of $BISON can reduce their trading and transfer expenses.
Portfolio Diversification: With access to more than 2,000 trading pairs, $BISON holders can diversify their portfolios without leaving the ecosystem.
Liquidity and Accessibility: The token is available on well-known decentralized exchanges, making it accessible to both experienced traders and newcomers.
3. How to Get StartedStep 1: Set Up a Solana-Compatible Wallet
Choose Your Wallet: Download Phantom or any other Solana-compatible wallet. For desktop, you can use the Google Chrome extension by visiting the official Phantom website.
Secure Your Recovery Phrase: During setup, store your recovery phrase in a safe location; never share this phrase with anyone.
Step 2: Fund Your Wallet with SOL
Direct Purchase: You can purchase SOL directly through the Phantom wallet using supported payment methods.
Transfer from Another Wallet: If you already have SOL in another wallet, transfer the desired amount to your new Phantom wallet address.
Exchange Purchase: Alternatively, buy SOL on an exchange (e.g., Binance, Coinbase) and send it to your Phantom wallet.
Step 3: Swap SOL for $BISON
Go to Raydium or Jup.ag: Open Raydium.io or Jup.ag in your browser and connect your Phantom wallet.
Select $BISON: Choose SOL as the token to swap from, and pick $BISON as the token to swap to.
Confirm Transaction: Review the swap details (amount, fees, and price impact). Confirm the transaction to complete your purchase of $BISON.
4. Trading Features
Order Types: Benefit from multiple order types (market, limit) offered through Raydium and other Solana-based DEX platforms.
Advanced Analytics: Utilize available charting tools to track price movements, historical data, and market trends.
Security Measures: Transactions are confirmed on the Solana blockchain, ensuring transparency and security.
5. Future Developments
Ecosystem Expansion: The team behind BisonSol plans to continuously expand utility by integrating new features and partnerships within the Solana ecosystem.
Community Governance: Potential future governance mechanisms may empower token holders to have a say in key decisions and platform upgrades.
SOCIALS :
2 notes
·
View notes
Text
How To Reduce 5G Cybersecurity Risks Surface Vulnerabilities

5G Cybersecurity Risks
There are new 5G Cybersecurity Risks technology. Because each 5G device has the potential to be a gateway for unauthorized access if it is not adequately protected, the vast network of connected devices provides additional entry points for hackers and increases the attack surface of an enterprise. Network slicing, which divides a single physical 5G network into many virtual networks, is also a security risk since security lapses in one slice might result in breaches in other slices.
Employing safe 5G Cybersecurity Risks enabled devices with robust security features like multi-factor authentication, end-to-end encryption, frequent security audits, firewall protection, and biometric access restrictions may help organizations reduce these threats. Regular security audits may also assist in spotting any network vulnerabilities and taking proactive measures to fix them.
Lastly, it’s preferable to deal with reputable 5G service providers that put security first.
Take On New Cybersecurity Threats
Cybercriminals often aim their biggest intrusions at PCs. Learn the characteristics of trustworthy devices and improve your cybersecurity plan. In the current digital environment, there is reason for worry over the growing complexity and frequency of cyber attacks. Cybercriminals are seriously harming businesses’ reputations and finances by breaking into security systems using sophisticated tools and tactics. Being able to recognize and address these new issues is critical for both users and businesses.
Threats Driven by GenAI
Malicious actors find it simpler to produce material that resembles other individuals or entities more authentically with generative AI. Because of this, it may be used to trick individuals or groups into doing harmful things like handing over login information or even sending money.
Here are two instances of these attacks:
Sophisticated phishing: Emails and other communications may sound much more human since GenAI can combine a large quantity of data, which increases their credibility.
Deepfake: With the use of online speech samples, GenAI is able to produce audio and maybe even video files that are flawless replicas of the original speaker. These kinds of files have been used, among other things, to coerce people into doing harmful things like sending money to online fraudsters.
The mitigation approach should concentrate on making sure that sound cybersecurity practices, such as minimizing the attack surface, detection and response methods, and recovery, are in place, along with thorough staff training and continual education, even if both threats are meant to be challenging to discover. Individuals must be the last line of defense as they are the targeted targets.
Apart from these two, new hazards that GenAI models themselves encounter include prompt injection, manipulation of results, and model theft. Although certain hazards are worth a separate discussion, the general approach is very much the same as safeguarding any other important task. Utilizing Zero Trust principles, lowering the attack surface, protecting data, and upholding an incident recovery strategy have to be the major priorities.Image Credit To Dell
Ransomware as a Service (RaaS)
Ransomware as a Service (RaaS) lets attackers rent ransomware tools and equipment or pay someone to attack via its subscription-based architecture. This marks a departure from typical ransomware assaults. Because of this professional approach, fraudsters now have a reduced entrance barrier and can carry out complex assaults even with less technical expertise. There has been a notable rise in the number and effect of RaaS events in recent times, as shown by many high-profile occurrences.
Businesses are encouraged to strengthen their ransomware attack defenses in order to counter this threat:
Hardware-assisted security and Zero Trust concepts, such as network segmentation and identity management, may help to reduce the attack surface.
Update and patch systems and software on a regular basis.
Continue to follow a thorough incident recovery strategy.
Put in place strong data protection measures
IoT vulnerabilities
Insufficient security makes IoT devices susceptible to data breaches and illicit access. The potential of distributed denial-of-service (DDoS) attacks is increased by the large number of networked devices, and poorly managed device identification and authentication may also result in unauthorized control. Renowned cybersecurity researcher Theresa Payton has even conjured up scenarios in which hackers may use Internet of Things (IoT) devices to target smart buildings, perhaps “creating hazmat scenarios, locking people in buildings and holding people for ransom.”
Frequent software upgrades are lacking in many IoT devices, which exposes them. Furthermore, the deployment of more comprehensive security measures may be hindered by their low computational capacity.
Several defensive measures, such assuring safe setup and frequent updates and implementing IoT-specific security protocols, may be put into place to mitigate these problems. These protocols include enforcing secure boot to guarantee that devices only run trusted software, utilizing network segmentation to separate IoT devices from other areas of the network, implementing end-to-end encryption to protect data transmission, and using device authentication to confirm the identity of connected devices.
Furthermore, Zero Trust principles are essential for Internet of Things devices since they will continuously authenticate each user and device, lowering the possibility of security breaches and unwanted access.
Overarching Techniques for Fighting Cybersecurity Risks
Regardless of the threat type, businesses may strengthen their security posture by taking proactive measures, even while there are unique tactics designed to counter certain threats.
Since they provide people the skills and information they need to tackle cybersecurity risks, training and education are essential. Frequent cybersecurity awareness training sessions are crucial for fostering these abilities. Different delivery modalities, such as interactive simulations, online courses, and workshops, each have their own advantages. It’s critical to maintain training sessions interesting and current while also customizing the material to fit the various positions within the company to guarantee its efficacy.
Read more on govindhtech.com
#Reduce5G#CybersecurityRisks#5Gservice#ZeroTrust#generativeAI#cybersecurity#strongdata#onlinecourses#SurfaceVulnerabilities#GenAImodels#databreaches#OverarchingTechniques#technology#CybersecurityThreats#technews#news#govindhtech
2 notes
·
View notes
Text
How to Hire a Social Media Hacker Safely: A Complete Guide
In today’s tech-driven world, social media accounts are more than just a place for socializing—they are gateways to personal and business data. Whether you're locked out of your account, worried about digital privacy, or need to strengthen your security, hiring a hacker might seem like a quick fix. However, it's important to approach this cautiously. In this guide, we'll explain how to safely and legally hire a social media hacker, what to look for, and the risks involved.
1. Why Hire a Social Media Hacker?
There are a variety of reasons why you might consider hiring a hacker for your social media needs. Some of the most common include:
Account Recovery: Losing access to a social media account due to hacking or forgotten passwords can be frustrating. A professional hacker can bypass recovery protocols and get you back in.
Security Audits: Ethical hackers can identify weaknesses in your social media security, helping you prevent future cyber-attacks.
Data Retrieval: For business purposes, some companies hire hackers to retrieve important information or gain insights into competitors.
While the idea of hiring a hacker might seem risky, when done ethically and legally, it can be a helpful resource in regaining control over your online assets.
2. What is a Professional Social Media Hacker?
A professional social media hacker is an expert skilled in identifying and exploiting weaknesses in social media platforms to recover accounts, enhance security, or gather data. These hackers fall into two categories:
White-Hat Hackers: Ethical hackers who work within legal boundaries. They are typically hired for account recovery, security testing, and digital protection services.
Black-Hat Hackers: Individuals who use their skills for malicious purposes, such as unauthorized access or data theft.
It's essential to make sure you're hiring a white-hat hacker to ensure the legality of their actions. White-hat hackers use legitimate methods to help you regain access or fortify your account.
3. How to Hire a Social Media Hacker
Finding a reliable social media hacker takes more than just a quick Google search. Here’s how you can find a legitimate hacker without falling for scams:
Freelance Platforms: Websites like Upwork, Freelancer, and Fiverr host professionals offering hacking and cybersecurity services. Be sure to check reviews and ask for verifiable past work.
Cybersecurity Firms: Many reputable companies specialize in ethical hacking services. Hiring through these firms ensures that you’re working with professionals who will operate within legal boundaries.
Hacker Forums: There are many online forums where ethical hackers offer their services. However, proceed with caution, as these forums can also be a breeding ground for scams.
Once you find a hacker, ask for credentials or proof of their experience with the platform you need help with, such as Facebook, Instagram, or Twitter.
4. The Benefits of Hiring a Professional Social Media Hacker
When you hire a social media hacker, you're not just gaining access to your account; you're investing in your online security and peace of mind. Here are the key benefits:
Quick Account Recovery: Forget the long, frustrating customer support routes. A professional hacker can help you regain access faster.
Improved Security: By running security checks and vulnerability assessments, hackers can help you secure your social media accounts and prevent future breaches.
Competitive Advantage: In business, accessing legally obtained data from competitors can help improve your strategies.
Hiring a hacker can be a valuable tool for both personal and professional needs, but only when done ethically.
5. Legal Risks of Hiring a Social Media Hacker
While hiring a hacker can solve a number of problems, it’s essential to understand the risks involved:
Illegal Hacking: Hacking someone else's social media account without permission is illegal and can result in serious legal consequences. Always make sure that your actions, and the actions of the hacker you hire, are within the legal framework.
Scammers: Unfortunately, there are many untrustworthy individuals who claim to be hackers but are really out to scam people. Be careful when sharing personal information, and only work with vetted professionals.
Ethical Concerns: Even if a hacker offers to retrieve information from someone else’s account, remember that doing so without consent is unethical and illegal.
Before you hire, ensure that the hacker’s actions will be lawful and ethical to avoid any legal trouble.
6. How to Protect Yourself When Hiring a Hacker
To safely hire a social media hacker, here are some best practices to follow:
Do Your Research: Take the time to verify the hacker’s credentials. Look at their previous work, ask for references, and check for any feedback from past clients.
Use Secure Communication: Always communicate securely with the hacker to protect your personal information. Avoid sharing sensitive data over unencrypted platforms.
Create a Clear Agreement: Before any work begins, have a formal contract that outlines the services to be performed and the legal limitations. This protects both parties and ensures that the work stays within ethical boundaries.
7. Hiring a Social Media Hacker: What to Expect
When working with a professional hacker, clear communication and expectations are essential. Here’s what to expect:
Transparent Pricing: The cost of hiring a hacker can vary depending on the complexity of the task. Be wary of hackers who offer extremely low rates, as they might not be legitimate.
Clear Communication: A professional hacker should explain the process clearly and answer any questions you have along the way.
Results: Whether you’re looking for account recovery or a security audit, a professional hacker should deliver results within the agreed-upon timeframe.
Conclusion: The Right Way to Hire a Social Media Hacker
Hiring a social media hacker can be an effective way to recover lost accounts, strengthen security, or gain strategic insights. However, it’s essential to hire a reputable, ethical hacker who operates within legal boundaries. By following the steps outlined in this guide, you can safely and legally hire a professional social media hacker to help with your digital needs.
For more information:
Hire a Hacker
Hire a Social Media Hacker
Professional Social Media Hacker
This article integrates the keywords "hire a hacker," "hire a social media hacker," and "professional social media hacker" naturally throughout the content, while keeping the information helpful and engaging for readers. It also includes hyperlinks to the desired website for further exploration, ensuring SEO indexability.
2 notes
·
View notes
Text
What Is Cloud Hosting?
When it came to hosting websites and applications, it used to be as simple as subscribing to a digital platform provider and, in essence, renting the usage of a single server or computer cluster. The existence of web hosting services dates back to the beginning of the internet itself. Over the course of the past ten years, cloud hosting has emerged as a major way for bringing digital assets online. Cloud hosting is a method in which the website or application is hosted on virtual servers that are distributed over the cloud.

A wide range of solutions for hosting websites and applications are available through Google Cloud. These solutions include the capability to register and maintain a domain, as well as the option to connect to a worldwide content delivery network in order to provide users with content that is optimized for performance and has the lowest possible latency.
Why should you use cloud hosting?
Website and application administrators are able to add or delete resources as needed thanks to cloud hosting. Additionally, this comprises additional random-access memory (RAM), storage capacity, or support services such as data storage or security. Hosting in the cloud offers increased dependability and flexibility at an affordable price. When compared to shared or dedicated hosting on a single server, cloud hosting offers greater data backup and disaster recovery capabilities.
The traditional dedicated server approach, which requires businesses to construct and run their own data centers, can be replaced with the cloud hosting model, which represents a more cost-effective option. In the traditional paradigm, servers and storage are located on the premises, and they are equipped with specialized hardware and virtual resources. This can be an expensive price for enterprises, both in terms of capital expenditures and running costs.
How does hosting on the cloud works?
When compared to regular web hosting, cloud hosting operates in a different manner. In the latter case, a centralized strategy is often utilized, in which a single web server is responsible for hosting several websites. Your website may experience a sudden increase in traffic from a neighbouring website if you utilize traditional hosting because the computer power and storage space are shared among customers of the hosting service. Cloud hosting services, on the other hand, make use of virtualization, which results in the partitioning of a physical server into several virtual servers. In order to host a website, it makes use of a network of servers, which guarantees superior performance and stability in comparison to hosting services that just employ a single server.
Several benefits of using cloud hosting –
Through cloud hosting, businesses are able to realize significant savings in terms of both capital and operational expenses. This is due to the fact that they do not have to pay a significant amount of money on the initial capital cost that is involved with the ownership and management of data centres. Another advantage is that the process of storing data for an extended period of time becomes less complicated, which eliminates the need for expensive administration of disks and tape systems.
Data protection advantages, such as high availability and disaster recovery, are available to businesses who make use of cloud hosting services. A hybrid approach, which combines elements of compute and storage resources that are located on the premises with those that are located in the environment of a best cloud hosting service provider, is preferred by many enterprises.
The cloud hosting also provides additional advantages as given below-
The price
When it comes to cloud hosting, the pay-as-you-go approach is frequently utilized, which means that the charges can be adjusted up or down based on the amount of usage. Web hosting, on the other hand, is often based on a set charge that is paid either monthly or annually.
Capacity to Grow
As a result of the fact that cloud hosting does not rely on a single server to store and distribute information, it is simple to scale up to match the requirements of a website or application. This is accomplished by spinning up additional servers across the cloud network when the quantity of usage increases.
Performance as well as dependability
It is possible to achieve high levels of reliability and uptime with best cloud hosting services because it makes use of a large number of servers that are dispersed over the cloud network. Other servers on the network are able to step in and continue to provide service in the event that one of the servers fails. Additionally, cloud hosting offers improved performance because it utilizes servers located in many countries to provide material to customers in a more expedient manner.
Security
The best cloud hosting service providers offer comprehensive physical and virtual security measures for the servers that are part of their network. These measures safeguard website and application data from being accessed by malicious actors. A number of different security layers are utilized in cloud hosting. These layers include firewalls, identity management and access control, Secure Sockets Layers (SSL) for data transmission, and more.
Flexibility
Best Cloud hosting gives users the ability to rapidly provision the parameters of virtual machines across the network, which gives them the freedom to pick the solution that is most suitable for any given circumstance.
Comparing web hosting to cloud hosting-
Web hosting in the traditional sense is often performed on a single server, which stores all of the files and content associated with the website of interest. When a user visits a domain, the documents and files are downloaded by a web browser associated with that domain.
Shared, dedicated, managed, and virtual private server (VPS) settings are the four basic types of environments that are available for web hosting accounts. When a single server is shared among a large number of different domains that are connected to the internet, this type of web hosting service is referred to as shared web hosting. On account of the fact that the various websites share the cost of the server, this is the most cost-effective of the available hosting solutions.
Shared hosting, on the other hand, restricts the scalability of individual websites because they are only able to utilize the resources of a single server. Dedicated hosting is a solution to this issue. In this type of hosting, a domain rents one or more servers that are not shared with any other websites or apps. However, the client is often responsible for administering the server on their own.
A managed hosting service is comparable to a dedicated hosting service; however, the hosting provider is responsible for all aspects of server management, including backup services, software and hardware upgrades, and security measures. Websites and apps that do not have the in-house skills necessary to maintain a server can benefit from managed hosting service because it streamlines the maintenance process.
There is a comparison of differences between best web hosting and affordable cloud hosting. First and foremost, when it comes to web hosting service, if a website requires additional resources as a result of growing demand, the customer is required to modify their service plan in order to accommodate the additional computing power, which creates a problem with scalability.
The best cloud hosting service provider makes it possible to distribute the content of a website across numerous virtual servers located in various areas. Additionally, it is simple to scale up the service in response to an increase in demand. As a result of this, cloud hosting is not only more durable and reliable than web hosting service, but it also provides greater freedom to alter the parameters according to the requirements of the situation.
How to choose best cloud hosting service provider?
It is important to take into consideration a variety of aspects when selecting a hosting service, including pricing, performance, scalability, reliability, security, and customer support. First, you should determine the unique demands and objectives of your company, and then you should examine the services offered by a number of different cloud hosting companies. Look for reviews and testimonials from previous customers to get an idea of how satisfied users are with the product.
Hosting in the cloud features-
Cloud computing allows for the deployment of applications and solutions on a network rather than on a single server located on the premises.
When user needs are met, resources can be scaled up.
Only the resources that are utilized by an organization are subject to payment.
SQL databases, including MySQL, as well as NoSQL databases can be supported via cloud hosting.
User interfaces (APIs), web portals, and mobile applications are utilized in order to automate and control solutions.
Conclusion-
When it comes to managing a website, affordable cloud hosting makes use of a virtual setup consisting of servers. When compared to conventional web hosting service, it provides enhanced reliability and reduces the likelihood of hardware failure and malfunction. The end result is consistent performance on the website.
For the construction of large-scale projects, such as enterprise websites, eCommerce businesses, social networks, and aggregator platforms, affordable cloud hosting is the best solution. In addition, a managed cloud hosting solution does not necessitate any prior technical expertise whatsoever.

Dollar2host Dollar2host.com
We provide expert Webhosting services for your desired needs
Facebook Twitter Instagram YouTube
2 notes
·
View notes
Text
Journey to AWS Proficiency: Unveiling Core Services and Certification Paths
Amazon Web Services, often referred to as AWS, stands at the forefront of cloud technology and has revolutionized the way businesses and individuals leverage the power of the cloud. This blog serves as your comprehensive guide to understanding AWS, exploring its core services, and learning how to master this dynamic platform. From the fundamentals of cloud computing to the hands-on experience of AWS services, we'll cover it all. Additionally, we'll discuss the role of education and training, specifically highlighting the value of ACTE Technologies in nurturing your AWS skills, concluding with a mention of their AWS courses.

The Journey to AWS Proficiency:
1. Basics of Cloud Computing:
Getting Started: Before diving into AWS, it's crucial to understand the fundamentals of cloud computing. Begin by exploring the three primary service models: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Gain a clear understanding of what cloud computing is and how it's transforming the IT landscape.
Key Concepts: Delve into the key concepts and advantages of cloud computing, such as scalability, flexibility, cost-effectiveness, and disaster recovery. Simultaneously, explore the potential challenges and drawbacks to get a comprehensive view of cloud technology.
2. AWS Core Services:
Elastic Compute Cloud (EC2): Start your AWS journey with Amazon EC2, which provides resizable compute capacity in the cloud. Learn how to create virtual servers, known as instances, and configure them to your specifications. Gain an understanding of the different instance types and how to deploy applications on EC2.
Simple Storage Service (S3): Explore Amazon S3, a secure and scalable storage service. Discover how to create buckets to store data and objects, configure permissions, and access data using a web interface or APIs.
Relational Database Service (RDS): Understand the importance of databases in cloud applications. Amazon RDS simplifies database management and maintenance. Learn how to set up, manage, and optimize RDS instances for your applications. Dive into database engines like MySQL, PostgreSQL, and more.
3. AWS Certification:
Certification Paths: AWS offers a range of certifications for cloud professionals, from foundational to professional levels. Consider enrolling in certification courses to validate your knowledge and expertise in AWS. AWS Certified Cloud Practitioner, AWS Certified Solutions Architect, and AWS Certified DevOps Engineer are some of the popular certifications to pursue.
Preparation: To prepare for AWS certifications, explore recommended study materials, practice exams, and official AWS training. ACTE Technologies, a reputable training institution, offers AWS certification training programs that can boost your confidence and readiness for the exams.
4. Hands-on Experience:
AWS Free Tier: Register for an AWS account and take advantage of the AWS Free Tier, which offers limited free access to various AWS services for 12 months. Practice creating instances, setting up S3 buckets, and exploring other services within the free tier. This hands-on experience is invaluable in gaining practical skills.
5. Online Courses and Tutorials:
Learning Platforms: Explore online learning platforms like Coursera, edX, Udemy, and LinkedIn Learning. These platforms offer a wide range of AWS courses taught by industry experts. They cover various AWS services, architecture, security, and best practices.
Official AWS Resources: AWS provides extensive online documentation, whitepapers, and tutorials. Their website is a goldmine of information for those looking to learn more about specific AWS services and how to use them effectively.
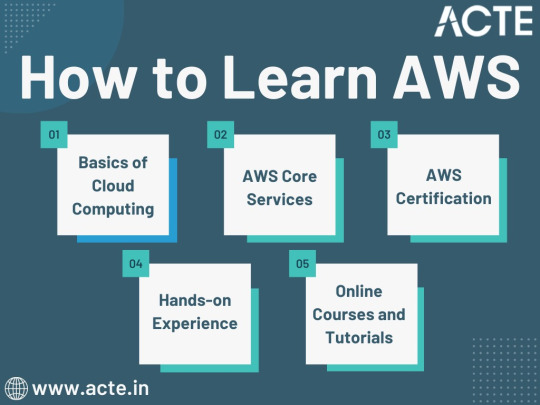
Amazon Web Services (AWS) represents an exciting frontier in the realm of cloud computing. As businesses and individuals increasingly rely on the cloud for innovation and scalability, AWS stands as a pivotal platform. The journey to AWS proficiency involves grasping fundamental cloud concepts, exploring core services, obtaining certifications, and acquiring practical experience. To expedite this process, online courses, tutorials, and structured training from renowned institutions like ACTE Technologies can be invaluable. ACTE Technologies' comprehensive AWS training programs provide hands-on experience, making your quest to master AWS more efficient and positioning you for a successful career in cloud technology.
8 notes
·
View notes
Text
Protecting Your Investments: The Vital Role of Fraud Investigation in Recovering from Crypto Scams
In today's digital world, cryptocurrencies have emerged as a highly sought-after investment option for both individuals and businesses. The allure of decentralized control and potential high returns has captivated many, leading to a surge in virtual currency adoption. Unfortunately, this surge has also brought about a rise in scams and fraudulent activities within the industry. The decentralized nature of cryptocurrencies makes it challenging to regulate and monitor, leaving investors vulnerable to exploitation. Countless cases of crypto scams have been reported in recent years, resulting in significant financial losses for victims. In such circumstances, it becomes imperative to safeguard your investments and take the necessary steps to recover any incurred losses. This is where fraud investigation plays a crucial role. In this article, we will explore the importance of fraud investigation in crypto scam recovery and its role in protecting your hard-earned investments. We will delve into various techniques and strategies employed in fraud investigation and how they aid in recovering stolen funds. So, let's delve into the ways you can safeguard your investments in the world of cryptocurrencies.
In today's digital era, where financial transactions predominantly occur online, the risk of falling victim to online scams and fraud is more prevalent than ever. As individuals and businesses invest in cryptocurrencies, the need to protect their assets becomes paramount. This is where the significance of online scam and fraud investigation comes into play. By enlisting the services of professional investigators specialized in crypto scam recovery, individuals and businesses can actively pursue the recovery of their lost or stolen crypto assets. These experts possess the knowledge and expertise required to trace and track transactions, identify fraudulent activities, and gather the necessary evidence for legal proceedings. Through thorough investigation, they can uncover the perpetrators behind these scams, ensuring that justice is served and that victims have an opportunity to reclaim their hard-earned investments. Safeguarding your investments with the assistance of fraud investigation is not only a proactive measure but also an essential one in today's complex and ever-evolving financial landscape.
Experiencing the loss or theft of your crypto assets can be a devastating ordeal, leaving you feeling helpless and frustrated. However, there are steps you can take to recover lost or stolen crypto assets. The first crucial step is to remain calm and avoid panicking, as this can cloud your judgment. Next, gather all relevant information about the incident, including transaction details, wallet addresses, and any other pertinent data. It is essential to report the theft or loss to the appropriate authorities, such as the police or relevant crypto exchange platforms, as soon as possible. Additionally, consider reaching out to cybersecurity experts or recovery services specializing in crypto assets to assist in tracking down and recovering your stolen funds. Remember to change your passwords and enhance your security measures to prevent future incidents. By taking swift and decisive action, there is a chance that you may be able to recover your lost or stolen crypto assets and protect yourself from further financial harm.
In today's digital landscape, safeguarding your crypto investments is of paramount importance. With the increasing prevalence of online scams and the potential for crypto scams leading to the loss or theft of digital assets, taking proactive measures to protect your investments is vital. Engaging in thorough online scam and fraud investigation can help you identify potential risks and prevent falling victim to fraudulent schemes. In the unfortunate event that you do become a victim of a crypto scam, it is crucial to seek professional assistance for crypto scam recovery. With their expertise and knowledge, these professionals can guide you through the complex process of recovering lost or stolen crypto, ensuring that you have the best chance of reclaiming your assets. By taking the necessary steps to safeguard your crypto investments today, you can mitigate the risks associated with online scams and protect your financial future.
In conclusion, as cryptocurrency continues to gain popularity, the threat of scams and frauds targeting unsuspecting investors also increases. It is crucial for individuals to safeguard their investments by remaining vigilant and conducting thorough research before making any financial decisions. In cases where fraud does occur, seeking the help of a professional fraud investigator can greatly increase the chances of recovering lost funds. By staying informed and taking necessary precautions, investors can protect their assets and contribute to a safer and more secure crypto marketplace.
3 notes
·
View notes
Text
Credit Repair Payment Solutions: Boosting Business with Streamlined Systems
Article by Jonathan Bomser | CEO | Accept-Credit-Cards-Now.com

In the fast-paced universe of credit repair, success hinges on two pivotal elements: effectiveness and efficiency. As credit repair experts, you are well-versed in the painstaking efforts required to rejuvenate credit scores for both individuals and businesses. Yet, to truly excel in this industry, it's imperative that your payment systems are not only secure and reliable but also finely tuned for high-risk transactions. In this piece, we'll delve into the game-changing potential of credit repair payment solutions, exploring how streamlined systems can propel your business to new heights. Importantly, we'll highlight how the adoption of the right payment processing strategies can bolster your credibility and fuel your expansion.
DOWNLOAD THE CREDIT REPAIR SOLUTIONS INFOGRAPHIC HERE
The Essence of Payment Processing At the core of any thriving credit repair enterprise lies the capacity to seamlessly accept credit card payments. Today's clients demand flexibility, and the ability to offer a range of payment options can significantly influence your business. This is especially pertinent in the high-risk transaction domain, which often presents unique challenges. By embracing dependable payment processing solutions tailored for high-risk scenarios, you not only meet your clients' expectations but exceed them, underscoring your commitment to their financial recovery.
Mastery of High-Risk Transactions Navigating the intricacies of high-risk merchant accounts and transactions can be treacherous without the right tools. This is where specialized payment processing systems, customized for high-risk situations, come to the fore. These systems are purpose-built to mitigate risk while optimizing the efficiency of credit repair payments. Equipped with robust fraud prevention mechanisms and advanced encryption, they create a secure environment that cultivates trust and longevity for both your clients and your business.
Pioneering E-Commerce in Credit Repair The digital revolution has reshaped the business landscape irrevocably. E-commerce has rapidly emerged as the favored channel for clients seeking credit repair services. To harness the full potential of this burgeoning market, you require an e-commerce payment gateway that seamlessly accommodates standard and high-risk credit card processing. By offering fluid online payment options, you unlock the gateway to a broader clientele, thereby expanding your outreach and influence.
Elevating Credibility via Efficiency Credibility serves as the bedrock of any credit repair enterprise. Clients must place unwavering trust in the meticulous handling of their sensitive financial data. Streamlined payment solutions not only augment transaction efficiency but also bolster the credibility of your services. When clients witness your investment in cutting-edge payment processing systems, they are more inclined to regard you as a trustworthy partner in their credit journey.
The CBD Challenge For those engaged in credit repair within the CBD industry, the challenges are particularly formidable. Given the persistent stigma surrounding CBD-related businesses, dependable payment processing is non-negotiable. An integrated CBD merchant account, coupled with high-risk payment solutions, can alleviate these challenges, enabling you to confidently accept credit card payments and fostering growth within this burgeoning sector.
youtube
Crafting a Tailored Resolution Recognizing the idiosyncratic demands of the credit repair sector, payment processing providers now offer bespoke solutions for merchants like you. Whether you engage in traditional credit repair, e-commerce operations, or CBD-related services, a payment processing system finely attuned to your field's intricacies can profoundly enhance your operations. This personalized approach ensures that you are not merely employing a system but harnessing a tool optimized precisely for your unique requisites.
In the credit repair realm, where success hinges on demonstrable results, the right payment processing system emerges as your most invaluable asset. By seamlessly integrating credit card processing, adept high-risk transaction management, and e-commerce capabilities, you elevate your enterprise's efficiency, credibility, and reach. It transcends the act of payment acceptance; it epitomizes the delivery of a seamless experience that reflects your unwavering commitment to your client's financial well-being. Embrace credit repair payment solutions that truly comprehend your industry, and witness your business flourish as you stride toward a more prosperous future.
#high risk merchant account#high risk payment gateway#high risk payment processing#merchant processing#credit card payment#payment processing#credit card processing#accept credit cards#payment#Youtube
17 notes
·
View notes
Text
Cyber Security Threat For Local Businesses
In this article learn the cyber security risks for Australian small businesses and how to protect your business future.
Australian local businesses face an ever-growing threat from cybercriminals. While many small business owners believe they're too insignificant to attract hackers, the reality is quite different. Cybercriminals often target smaller enterprises precisely because they tend to have weaker security measures in place. This blog post will explore the cyber dangers that small businesses in Australia may face and offer some practical advice on how to protect your livelihood.
The Growing Menace of Cyber Attacks
Why Small Businesses Are Targets
You might think your local shop or service isn't worth a hacker's time, but you'd be wrong. Cybercriminals often view small businesses as low-hanging fruit. Here's why:
1. Limited resources for cybersecurity
2. Less sophisticated defence systems
3. Valuable customer data
4. Potential gateway to larger partner companies
Common Cyber Threats to Watch Out For
Ransomware Blackcat Ransomware Gang.

Ransomware attacks have skyrocketed in recent years. These nasty pieces of software encrypt your data and demand payment for its release. For a small business, this can be devastating. Imagine losing access to your customer database or financial records overnight!
Phishing Scams
Phishing remains one of the most common ways cybercriminals gain access to your systems. They send seemingly legitimate emails that trick you or your staff into revealing sensitive information or downloading malware.
Data Breaches
Small businesses often store valuable customer data, making them prime targets for data breaches. A breach can result in hefty fines under Australian privacy laws and irreparable damage to your reputation.
Protecting Your Business from Cyber Threats
Essential Security Measures
1. **Use strong, unique passwords**: Implement a password policy that requires complex passwords and regular changes.
2. **Keep software updated**: Regularly update your operating systems, applications, and security software to patch vulnerabilities.
3. **Educate your staff**: Your employees are your first line of defence. Train them to recognise and report suspicious emails or activities.
Invest in Cybersecurity
While it might seem costly, investing in cybersecurity is far cheaper than dealing with the aftermath of an attack. Consider these steps:
1. **Install and maintain firewalls**: These act as a barrier between your internal network and external threats.
2. **Use encryption**: Encrypt sensitive data, especially if you store customer information.
3. **Implement multi-factor authentication**: This adds an extra layer of security beyond just passwords.
Create a Cybersecurity Plan
Don't wait for an attack to happen before you start thinking about cybersecurity. Develop a plan that includes:
1. Regular risk assessments
2. Incident response procedures
3. Data backup and recovery strategies
The Cost of Ignoring Cybersecurity
Failing to address cybersecurity can have dire consequences for your business:
1. Financial losses from theft or ransom payments
2. Damage to your reputation and loss of customer trust
3. Legal consequences for failing to protect customer data
4. Potential business closure due to inability to recover from an attack
Don't become another statistic in the growing list of small businesses crippled by cyber attacks. Take action today to protect your business, your customers, and your future.
Remember, in the digital age, cybersecurity isn't just an IT issue—it's a critical business concern that demands your attention and investment.
Kelly Hector creator of YouTube channel focused on cyber security risks and local marketing
#cyber security awareness#local business#digital marketing#cyberattack#cybersecurity#digitalworldvision.online
1 note
·
View note
Text
Crypto recovery review
As of my last update in January 2022, I can't provide specific reviews of individual crypto recovery review services since I don't have access to real-time information or reviews beyond that point. However, I can offer guidance on what to consider when evaluating crypto recovery services and how to approach the recovery process:
Reputation and Trustworthiness: Research the reputation and track record of the crypto recovery service. Look for reviews and testimonials from previous clients. Verify the legitimacy of the company by checking if they are registered, licensed, or accredited by relevant authorities.
Transparency: A trustworthy crypto recovery service should be transparent about their process, fees, and success rates. Avoid services that make unrealistic promises or guarantees of recovery, as the outcome of recovery attempts can vary depending on the circumstances.
Experience and Expertise: Look for a recovery service that has experience and expertise in dealing with cryptocurrency-related issues, such as lost funds, stolen wallets, or scam recovery. Ask about the qualifications and background of the team members who will be handling your case.
Security Measures: Ensure that the crypto recovery service has robust security measures in place to protect your sensitive information and funds. Ask about their data security practices and how they handle client confidentiality.
Communication: Choose a recovery service that maintains open and responsive communication throughout the recovery process. They should provide regular updates on the status of your case and be available to address any questions or concerns you may have.
Legal Compliance: Verify that the crypto recovery service operates in compliance with relevant laws and regulations. Avoid services that engage in illegal or unethical practices, such as hacking or unauthorized access to accounts.
Cost: Understand the fee structure of the recovery service and ensure that it is transparent and reasonable. Be wary of services that require upfront payment or charge exorbitant fees regardless of the outcome of the recovery attempt.
Alternative Options: Consider exploring alternative options for recovering your lost funds, such as seeking assistance from law enforcement agencies, regulatory authorities, or legal professionals specializing in cryptocurrency law.
Ultimately, when choosing a crypto recovery service, it's essential to exercise caution, conduct thorough research, and trust your instincts. If you're unsure about a particular service, consider seeking recommendations from trusted sources or consulting with professionals in the cryptocurrency industry.
3 notes
·
View notes
Text
How Your Web Hosting Choice Impacts e-Commerce Marketing Success
One of the most important parts of e-commerce is web hosting. The majority of online retailers view it as the foundation or heart of e-commerce. It makes e-commerce more prominent and takes designers to new areas. Today, we'll delve into the specifics of website hosting to learn about its advantages for entrepreneurs.
To give you a head start, all bloggers can thrive in the dynamic atmosphere surrounding the e-commerce web hosting industry. However, it's safe to examine web hosting from a basic standpoint and get a quick rundown of the state of web hosting globally before delving deeply into its advantages.

What is Web hosting for e-commerce Business?
Anyone who hears about e-commerce web hosting will likely want to know what it is and what it involves. Since there isn't a single web hosting option that works for all e-commerce websites, the idea of e-commerce web hosting might be complicated. On the other hand, e-commerce web hosting is the term used to describe a service provided to e-commerce websites by web hosting providers.
To put it simply, web hosting for e-commerce refers to the process whereby a web hosting provider provides a server to an e-commerce website, simplifying the process of storing and managing files on the website. Put differently, a web hosting provider offers servers that you can buy or rent. The server can be used for a number of purposes, including database support, traffic management, product delivery, transaction processing, and optimising consumer security.
What is E-commerce business?
A company that generates revenue through online sales of goods or services is known as an e-commerce business. A business that engages in e-commerce offers a range of goods and services via online channels. These can include digital things like software, eBooks, and online courses, as well as tangible items like apparel, electronics, and home furnishings. E-Commerce businesses may also provide services like digital marketing, event tickets, and trip bookings. A wide range of goods and services are available for purchase and sale online under the umbrella of e-commerce.
Factors that indicate the success of e-commerce marketing impacted by web hosting-
Website Performance- Your website's dependability and speed are essential to the success of e-commerce. Research has indicated that a little one-second lag in page load times can lead to a significant decline in conversion rates. The setup of your best web hosting provider and server performance have a direct impact on how quickly your website loads. Choosing a reputable hosting company may guarantee quick loading times, lower bounce rates, and enhance user experience with sturdy servers and optimised performance.
Uptime and Reliability- For e-commerce companies, downtime may be disastrous since it can result in lost revenue, tarnished reputations, and diminished client loyalty. Maintaining a dependable online presence depends heavily on your best web hosting provider's uptime guarantee. Seek suppliers who guarantee 99.9% uptime or greater in order to reduce the possibility of website failures. Additionally, take into account their customer service responsiveness and disaster recovery plans to ensure prompt resolution of any potential problems.
Security Measures- In e-commerce, security plays a major role in communicating sensitive client data, including payment details. To safeguard your website and client data, your hosting company should implement strong security measures, such as firewalls, malware scanners, SSL certificate encryption, and frequent backups. In addition to undermining your company's credibility, a breach erodes consumer confidence and may have legal effects.
Scalability and Growth Potential- Your hosting requirements will grow along with your e-commerce business. You may store more data, trades, and traffic with the best hosting solution without sacrificing performance. Your hosting company should help you expand, whether that means adding new features or seamlessly updating server capacity. Scalability ensures that your website won't experience any hiccups or slowdowns when dealing with unforeseen traffic surges during promotional events or seasonal peaks.
Search Engine Optimization (SEO)- When evaluating websites, search engine algorithms consider factors including mobile friendliness, security, uptime, and speed. Choosing the best web hosting provider has a favourable impact on your SEO efforts, increasing your website's exposure and organic traffic. Conversely, poor search engine rankings can cause frequent failures, slow page loads, or security flaws, which can reduce your website's exposure and clientele.
Customer Experience and Satisfaction- Maintaining a consistent online purchasing experience is essential for client retention and pleasure. Your choice of the best hosting solution directly impacts checkout procedures, general usability, and website navigation. A well-designed website that loads quickly and experiences little downtime enhances user experience, encouraging return visits and building brand loyalty. However, a bad hosting decision can annoy clients, resulting in abandoned carts and unfavourable reviews.
Cost-Effectiveness- Although choosing the cheapest hosting service may seem enticing, it's important to consider the costs and advantages over the long run. Purchasing high-quality hosting may cost more upfront, but it will ultimately save you money by preventing income loss from server outages, hacks, or subpar operations. To determine which hosting plan is appropriate for your e-commerce business, estimate its features, dependability, and scalability.
Reliable Technical Support: Flaws and delays are common in the realm of online shopping. Despite your best efforts to avoid them, there's always a chance they'll happen and interfere with your e-commerce store's regular business operations. You must address these hiccups as soon as possible because they could make your clients unhappy. Technical problem-solving may be different from everyone's taste. To resolve such problems, you want a technical specialist. Nonetheless, you can always rely on your web host to assist you when needed. Make sure the affordable web hosting company you choose will support you in the event of technical difficulties. To address your technological issues, most web hosting providers have a strong technical support staff that is available around the clock.
Large Bandwidth and Storage: You should expect a lot of visitors to your e-commerce site, especially if your digital marketing tactics are effective. To keep customer information and other important details, you will also want a large amount of file space. Searching for external storage does not have to cost extra. A web host will be available for you. With its generous bandwidth and file storage options, the best hosting solution for e-commerce sites will take care of any storage issues.
Easy Cart-Shopping: Using a shopping cart improves and enhances the shopping experience. With a shopping cart, customers may select products they want to buy and then check them out at the register to make the final payment. They will remove the unwanted items from the cart and leave only the necessary items. The majority of e-commerce service providers provide easy-to-use and safe gateways for shopping carts. Make sure the web hosting provider you choose for your e-commerce store has a shopping cart feature for your website.
With Web hosting, the financial Burden Shifts to Someone else: We support e-commerce web hosting because it frees e-merchants from administrative and financial obligations. The web host takes on all of the associated financial costs of running your online store, including security patches, system updates, and system configuration. You redirect the time, funds, and resources you would have liked to employ for self-hosting to other areas of your company.
Web Hosting Comes with Lots of Customizable Features: Early hosted e-commerce platforms needed more flexibility when it came to software as a service (SaaS). That was true at the time, but times have changed drastically since then, and e-commerce web hosting solutions are now incredibly flexible. Customisation with a web hosting firm has the benefit that all coding and development will be handled by the technical professionals of the service provider. However, not all e-commerce web hosting is adaptable and provides customisable options, just as with all the other advantages. If you conducted your homework and selected a flexible one, it would be beneficial. It's crucial to look for e-commerce web hosting companies that work well with e-commerce app developers when looking for solutions for your website. This will guarantee that all technical details, including app development, meet your needs and help your customers have a flawless online shopping experience.
Timely Deployment: Time is of the importance in e-commerce. There is nothing better than web hosting providers' speed-to-market convenience. You can be certain that your e-commerce store will be up and operating quickly when you host it. In other words, web hosting makes your e-commerce websites as quickly accessible to potential clients as possible. If you want to self-host, however, the situation is different because there are expensive delays and downtimes.
You Get to Enjoy the Benefits of Sophisticated Architecture: The benefit of employing a hosting platform for your online business is that all customers have access to its excellent infrastructure. Put differently, having your e-commerce store hosted allows your company to have additional e-commerce features. To unlock the features required for your e-commerce store, all you have to do is work with your hosting provider. Furthermore, the hosting company you use will always be adding new features that you can access with just a click of a button.
Conclusion-
The success of your e-commerce marketing initiatives is greatly influenced by the web hosting service you choose. Every aspect of your online business is highly dependent on the capabilities of your hosting provider, whether it is for assuring peak website performance, strong security measures, smooth scalability, or improved customer experience. When you choose your hosting provider carefully, keeping in mind aspects like security, speed, scalability, and dependability, you create a solid base for your e-commerce company's expansion and the capacity to succeed in the face of intense online competition.

Janet Watson
MyResellerHome MyResellerhome.com We offer experienced web hosting services that are customized to your specific requirements. Facebook Twitter YouTube Instagram
1 note
·
View note
Text
Discuss How Web Development Services Can Benefit Startups

Web Development for Startups: Discuss how web development services can benefit startups, from MVP development to scaling a digital presence.
Startups, often characterized by limited resources and a passion for innovation, have a unique set of challenges and opportunities. In the digital age, web development services are a vital component for startups looking to bring their vision to life and achieve growth. In this article, we’ll explore how web development services can benefit startups, from Minimum Viable Product (MVP) development to scaling a robust digital presence.
1. MVP Development: Turning Ideas into Reality
Minimum Viable Product (MVP) development is a cornerstone for startups. It involves creating a simplified version of your product with the core features that solve a specific problem or address a unique need. Web development plays a crucial role in this initial phase by:
Rapid Prototyping: Web developers can quickly create functional prototypes that allow startups to test and validate their ideas with minimal investment.
User Feedback: MVPs are an opportunity to gather valuable user feedback, enabling startups to refine and improve their product based on real-world usage.
Cost Efficiency: Developing a web-based MVP is often more cost-effective than building a complete mobile application or software platform, making it an ideal starting point for startups with limited budgets.
2. Scalability: Preparing for Growth
As startups gain traction and user demand increases, scalability becomes a critical concern. Effective web development services can help startups prepare for growth by:
Scalable Architecture: Web developers can design and implement scalable architecture that allows the platform to handle increased traffic and data without performance degradation.
Database Optimization: Proper database design and optimization are essential for ensuring that the system can grow smoothly as more users and data are added.
Load Balancing: Load balancing distributes web traffic across multiple servers, ensuring that the system remains responsive and available, even during high-demand periods.
3. Mobile Responsiveness: Reaching a Wider Audience
With mobile device usage surpassing desktops, it’s essential for startups to have a web presence that is responsive and mobile-friendly. Web development services can ensure that your website or web application:
Adapts to Different Screens: A responsive design ensures that your site functions and looks good on various devices and screen sizes, from smartphones to tablets.
Improved User Experience: Mobile-responsive websites provide a seamless and enjoyable user experience, enhancing engagement and reducing bounce rates.
Enhanced SEO: Google and other search engines prioritize mobile-responsive websites in search results, potentially boosting your startup’s visibility.
4. User-Centric Design: Building Trust and Loyalty
A user-centric design is essential for startups looking to build trust and loyalty. Web development can help in the following ways:
Intuitive User Interface (UI): A well-designed UI simplifies user interaction and navigation, making the product user-friendly.
User Experience (UX): An optimized UX ensures that users enjoy using your product, leading to increased satisfaction and loyalty.
Branding and Consistency: Web developers can create a design that reflects your brand identity and maintains consistency throughout the user journey.
5. Security and Data Protection: Safeguarding User Information
For startups, maintaining the security and privacy of user data is paramount. Web development services can ensure that your platform is secure by:
Implementing Encryption: Secure Sockets Layer (SSL) encryption and other security measures protect data transmitted between users and your server.
Data Backup and Recovery: Regular data backups and recovery procedures are vital for safeguarding information and minimizing data loss in case of unexpected events.
Authentication and Authorization: Implementing robust authentication and authorization mechanisms ensures that only authorized users can access sensitive data.
Conclusion: The Road to Startup Success
Web development is a driving force behind the success of startups. From MVP development to scalability, mobile responsiveness, user-centric design, security, and privacy, web development services provide the foundation for startups to innovate and grow. By partnering with skilled web developers and investing in their digital presence, startups can create a compelling and competitive edge in today’s dynamic business landscape.
Source:
#kushitworld#india#saharanpur#itcompany#seo#seo services#webdevelopment#digitalmarketing#websitedesigning
4 notes
·
View notes
Text

Who We Are
At WasteMaterial.in, we are more than just scrap buyers. We are sustainability partners for industries, businesses, institutions, and households looking to dispose of their scrap responsibly and profitably. Our team is committed to providing transparent, environmentally friendly, and legally compliant scrap buying services across India.
As one of the top-rated scrap buyers in India, we help our clients turn waste into value while ensuring minimal environmental impact. Whether you’re dealing with industrial scrap, old household items, or electronic waste, we offer competitive rates and quick service.
Why Sell Your Scrap to Professional Buyers?
Scrap materials like metals, plastics, paper, and e-waste are often seen as waste, but they hold significant value when recycled correctly. However, selling scrap to unverified or informal buyers can lead to legal issues, safety concerns, and missed opportunities for maximum value recovery.
By partnering with authorized scrap buyers in India like WasteMaterial.in, you get:
Fair pricing based on current market rates
Hassle-free pickup and logistics
Proper documentation and receipts
Eco-friendly recycling and disposal
Compliance with government norms and environmental laws
What Types of Scrap Do We Buy?
We deal in a wide range of scrap categories to serve different industries and sectors. Some of the common types of scrap we buy include:
1. Metal Scrap
We buy ferrous and non-ferrous metal scraps such as iron, steel, copper, aluminum, brass, zinc, and more. Whether it’s leftover construction scrap or industrial machinery parts, we ensure optimal pricing and proper recycling.
2. E-Waste
As certified e-waste handlers, we buy old computers, laptops, mobile phones, printers, cables, batteries, and other electronic items. We ensure secure data destruction and environmentally sound recycling methods.
3. Plastic Scrap
We collect all grades of plastic waste, including HDPE, LDPE, PET, and PVC. Our recycling process helps reduce the burden of plastic pollution in landfills and oceans.
4. Paper and Cardboard
WasteMaterial.in also buys paper waste, including newspaper, office documents, cardboard boxes, books, and magazines — ideal for schools, offices, and printing presses.
5. Industrial and Commercial Scrap
We handle bulk scrap from manufacturing units, construction sites, warehouses, and retail businesses. Our scalable solutions make us a trusted partner for large-scale scrap management.
Why WasteMaterial.in is Among the Best Scrap Buyers in India
Here’s what sets us apart from the rest:
Pan-India Network: We operate across major cities and regions, offering on-site pickup services and customized collection schedules.
Competitive Prices: Our team monitors market rates daily to offer you the best price for your scrap materials.
Eco-Friendly Disposal: We prioritize sustainability. All materials are processed in compliance with environmental regulations.
Quick Turnaround: Fast responses, timely pickups, and efficient scrap clearance are part of our service promise.
Trusted by Thousands: From households to corporates, hundreds of clients trust WasteMaterial.in for reliable scrap selling solutions.
How It Works
Selling your scrap to WasteMaterial.in is simple:
Visit Our Website: Go to https://wastematerial.in and fill out our contact form or call us directly.
Get a Quote: Tell us what type of scrap you have and in what quantity. We’ll provide a competitive price instantly.
Schedule a Pickup: We’ll arrange a convenient time for our team to collect the scrap from your location.
Weigh and Pay: On-site weighing ensures transparency. We pay instantly through your preferred payment method.
Recycle Responsibly: Your scrap is processed and recycled through certified channels, and we provide documentation on request.
Partner with WasteMaterial.in Today
Whether you’re a business with regular scrap output or a household looking to get rid of old materials, WasteMaterial.in is your go-to destination for scrap buyers in India. With our expertise, infrastructure, and ethical practices, we help you manage waste better and earn more from it.
Join hundreds of satisfied customers who’ve turned their scrap into value with us.
Contact Us Now 📞 Call: [7829613504] 🌐 Website: https://wastematerial.in 📩 Email: [[email protected]]
WasteMaterial.in — India’s Trusted Name Among Scrap Buyers. Recycle Smart. Recycle with Us.
0 notes